Cyber Security is Hard
But, how to make sure everyhting is covered?
Standards and frameworks
Different frameworks guide cyber risk management -each with its own focus and adoption.
| Framework | Focus | Adoption / Use Case |
|---|---|---|
| NIST CSF 2.0 | Outcome-based, flexible, governance-driven | Widely used; adaptable to any sector |
| ISO/IEC 27001 | International ISMS, compliance & certification | Global; formal audits & certification |
| OCTAVE | Risk assessment, scenario-driven | Critical infrastructure & large orgs |
NIST CSF 2.0
Helpsorganisations manage andreducecybersecurityrisk- Built around six core functions
Basedon recognisedstandardsand best practiceProvidesa clear method for assessingmaturityand improvingcontrols- Aligns well with ISO/IEC 27001 (next week)
NIST Components
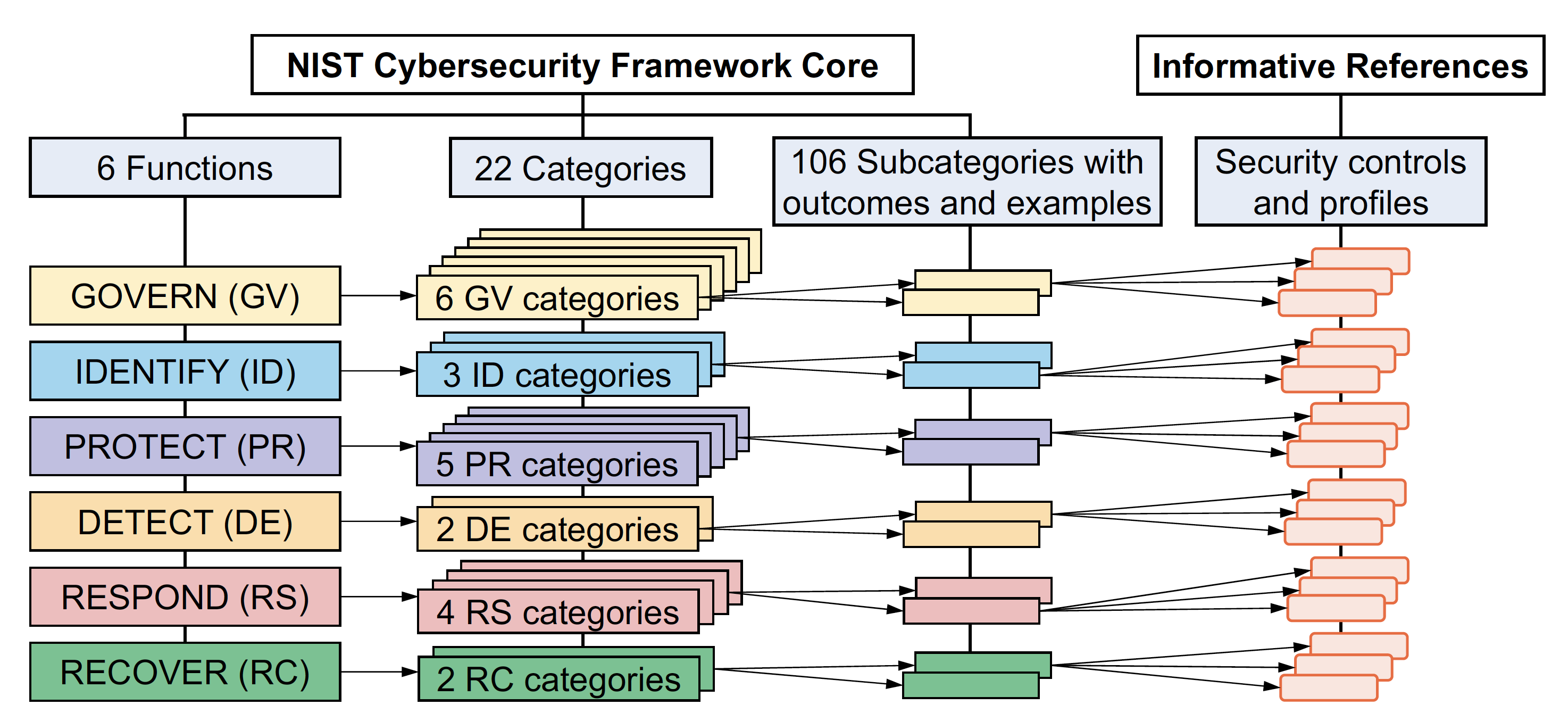
- A - CSF Core
- Functions → Categories → Subcategories (outcomes)
- B - Profiles
- Describe Current vs Target cybersecurity posture
- Support gap analysis
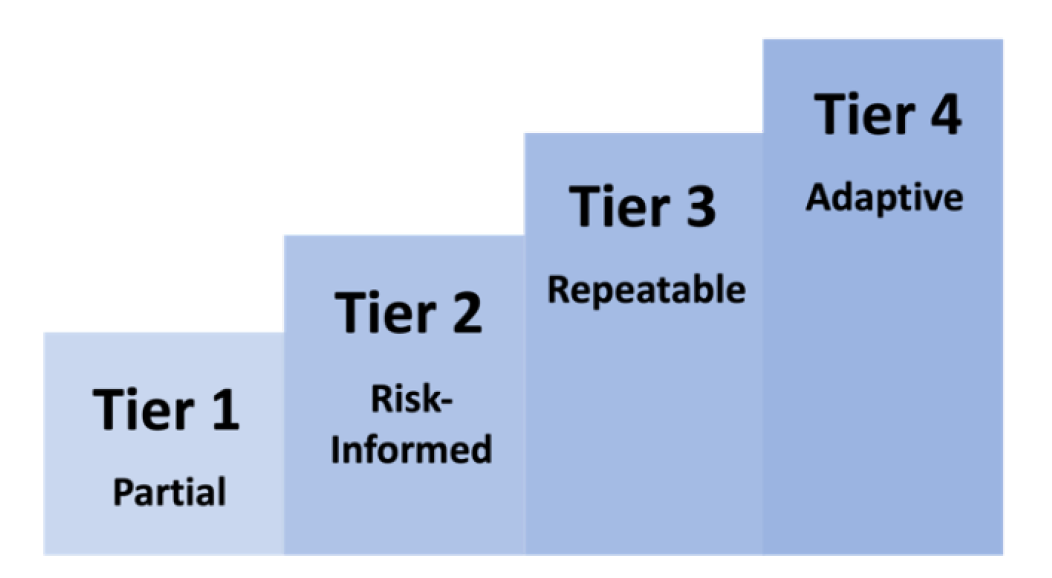
- C - Tiers
- Characterise maturity of risk governance & management
- From Tier 1 (Partial) → Tier 4 (Adaptive)
A. NIST CSF 2.0 - The Core
What you need to do.
|
|
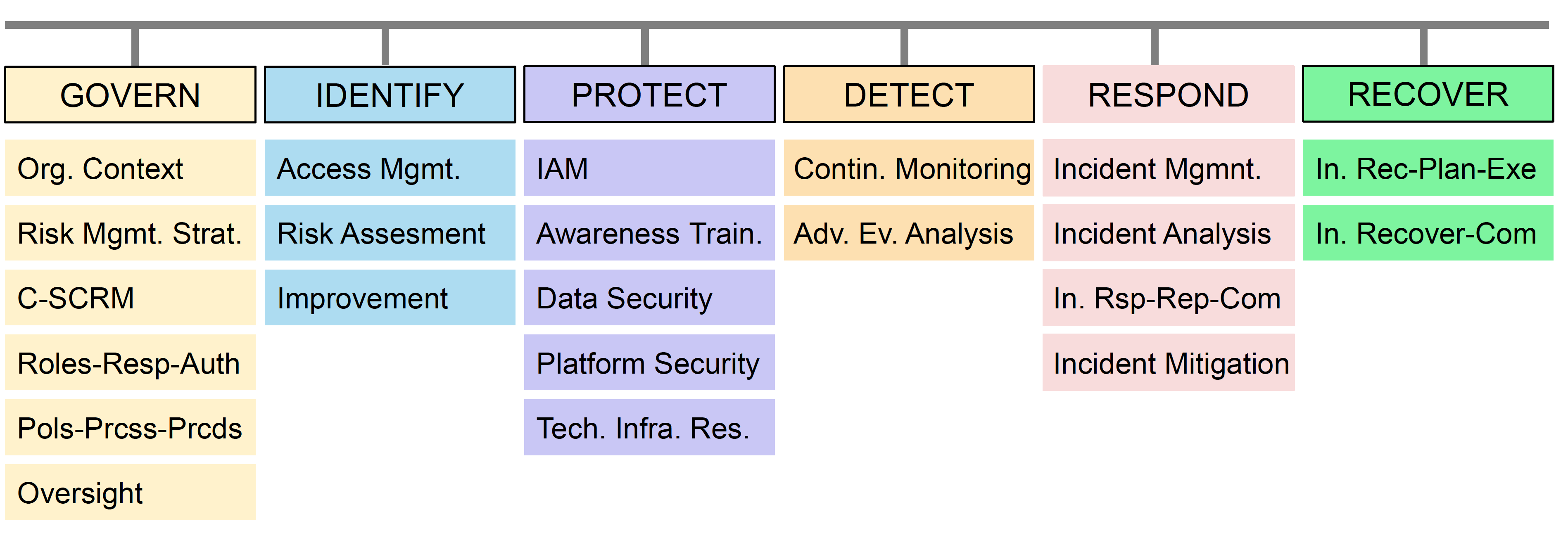
1. GOVERN (GV)
Categories (high-level outcomes):
- Organizational Context (GV.OC)
- Risk Management Strategy (GV.RM)
- Roles, Responsibilities, and Authorities (GV.RR)
- Policy (GV.PO)
- Oversight (GV.OV)
- Cybersecurity Supply Chain Risk Management (GV.SC)
Example: Define a supply chain risk policy requiring vendors to comply with ISO/IEC 27001.
2. IDENTIFY (ID)
Categories:
- Asset Management (ID.AM)
- Risk Assessment (ID.RA)
- Improvement (ID.IM)
Example: Maintain an updated inventory of cloud servers and assess them for vulnerabilities quarterly.
3. PROTECT (PR) (CIA)
Categories:
- Identity Management, Authentication, and Access Control, Backup (PR.AA)
- Awareness and Training (PR.AT)
- Data Security (PR.DS)
- Platform Security (PR.PS)
- Technology Infrastructure Resilience (PR.IR)
Example: Enforce multi-factor authentication (MFA) for all staff and provide annual phishing awareness training.
4. DETECT (DE)
Categories:
- Continuous Monitoring (DE.CM)
- Adverse Event Analysis (DE.AE)
Example: Use a SIEM system to detect unusual login attempts and analyse logs for signs of compromise.
5. RESPOND (RS)
(More to this in the last week with incident response)
Categories:
- Incident Management (RS.MA)
- Incident Analysis (RS.AN)
- Incident Response Reporting and Communication (RS.CO)
- Incident Mitigation (RS.MI)
Example: Activate the incident response plan during a ransomware attack, isolate infected systems, and notify stakeholders.
6. RECOVER (RC)
Categories:
- Incident Recovery Plan Execution (RC.RP)
- Incident Recovery Communication (RC.CO), e.g. Backup
Example: Restore critical services from tested backups and update customers with regular recovery progress reports.
NIST: Functions and 22 categories
Activity 1: Classify Controls into CSF Functions
Pick the correct NIST CSF Function for each row.
| Control | Govern | Identify | Protect | Detect | Respond | Recover |
|---|---|---|---|---|---|---|
| 1. Multi-factor authentication | ||||||
| 2. Asset inventory | ||||||
| 3. SIEM log analysis | ||||||
| 4. Backup restoration testing | ||||||
| 5. Security awareness training | ||||||
| 6. Patch management | ||||||
| 7. Vendor risk review | ||||||
| 8. Incident notification |
B. CSF Profiles
Describean organisation’spostureagainst CSFoutcomes- Help
assess,prioritiseandcommunicatecybersecurityneeds - Built with context such as mission, stakeholders and threat landscape
Types of Profiles
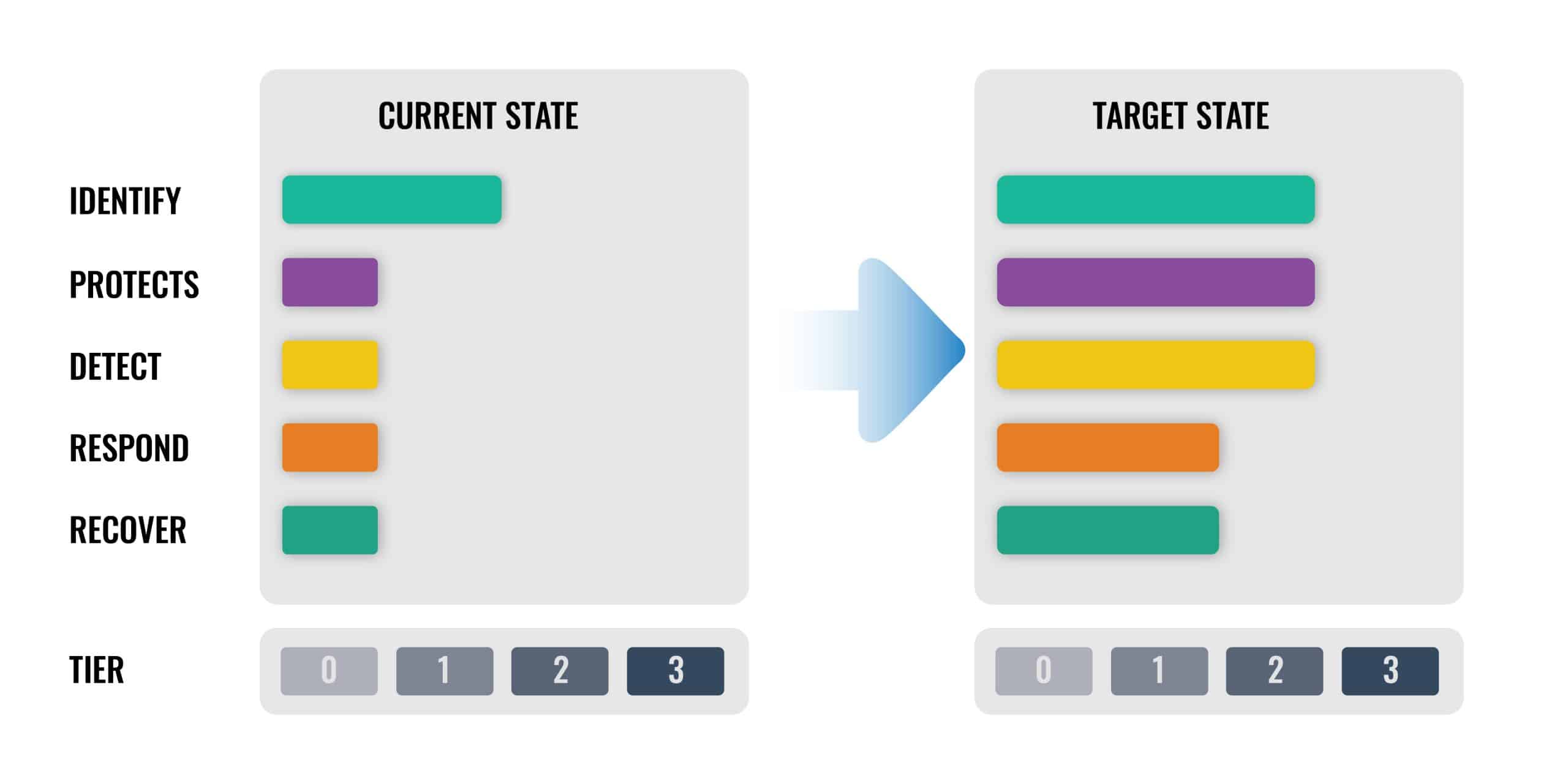
- Current Profile: What the organisation achieves today
- Target Profile: Desired outcomes for future capability
- Community Profile: Shared baseline for a sector or use case
B. CSF Profiles: In a nutshell
CSF Profile - Lifecycle Steps
Profiles describe what outcomes you achieve.
|
🔄 Continuous improvement cycle |
C. CSF Tiers
Tiers describe how mature your governance and processes are when achieving those outcomes.
|
➡️ Tiers = levels of maturity in governance & risk practices ➡️ Provide progressive targets for improving cybersecurity posture |
Building a CSF Profile with Tiers
| Step | Action | Outcome |
|---|---|---|
| 1 | Review current alignment with CSF Functions & Categories | Understand present capabilities |
| 2 | Assign each Function/Category to a Tier (1-4) | Measure current maturity |
| 3 | Combine with business objectives | Define the Current Profile |
| 4 | Identify desired outcomes & maturity levels | Define the Target Profile |
| 5 | Compare Current vs Target | Identify gaps & required improvements |
| 6 | Document improvements in a roadmap | Action plan to move toward Target Profile |
Example – CSF Profiles with Tiers
A university IT department manages staff and student data. Backups exist but are not encrypted. Logs are collected but rarely monitored. There is no formal incident response plan.
Applying the CSF Profile and Tiers
| Step | What you do | Example for the university |
|---|---|---|
| 1 | Review current alignment | Focus on PR.DS (Data Security) and RS.MA (Incident Management) |
| 2 | Assign Current Tiers | PR.DS = Tier 2 (basic controls) RS.MA = Tier 1 (ad hoc response) |
| 3 | Define Current Profile | Limited encryption and weak incident handling |
| 4 | Define Target Profile | PR.DS → Tier 3 (encrypted backups, monitoring) RS.MA → Tier 3 (formal IR plan and testing) |
| 5 | Identify gaps | No encryption, no IR plan, unclear roles |
| 6 | Create a roadmap | Q2: Implement encryption Q3–Q4: Develop IR plan, assign roles, test annually |
Activity: CSF Profiles and Tiers
A small university department has limited budget and no dedicated SOC. Backups are done monthly, logs are collected but not reviewed, and there is no formal incident response plan. Basic MFA is enabled for staff.
Task: estimate the Current Tier and Target Tier for each CSF Category below.
| CSF Category | Current Tier (1-4) | Target Tier (1-4) | Gap / Comment |
|---|---|---|---|
| PR.DS (Data Security) | |||
| DE.CM (Continuous Monitoring) | |||
| RS.MA (Incident Management) |
NIST: Issue
The NIST CSF defines what outcomes an organisation should achieve.
But it does not show:
- Which assets those outcomes apply to
- Who is responsible for each area
- How to spot gaps across devices, applications, networks, data and users
The Cyber Defense Matrix to the rescue.
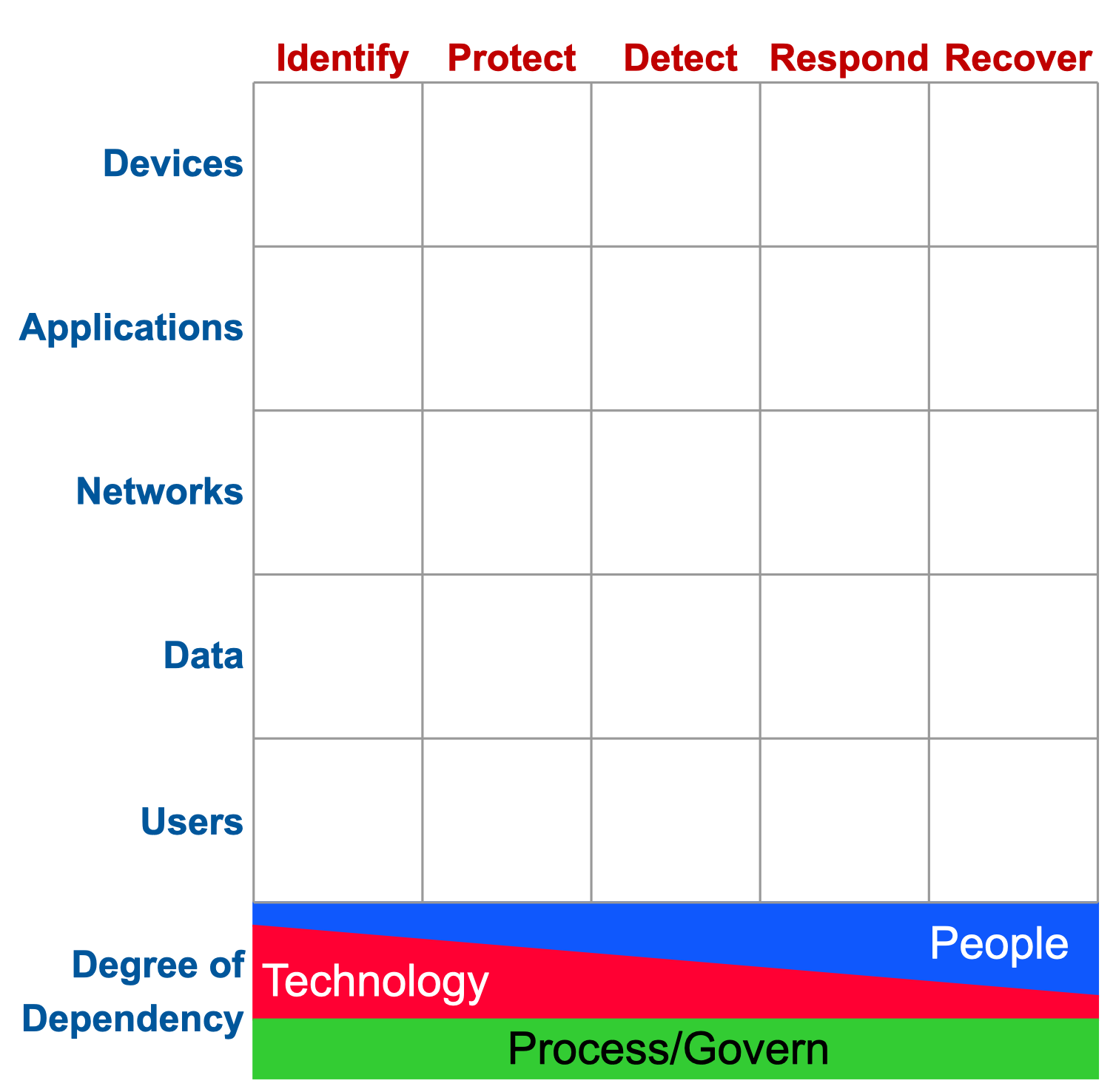
The Cyber Defense Matrix
|
The Cyber Defense Matrix expands NIST CSF with a two‑dimensional model:
Purpose
|
|
CDM Asset Classes
- Devices - Hardware, firmware, OS, vendor apps, networking gear
- Applications - In-house business apps and services
- Networks - Routing, DNS, PKI, firewalls, VPNs
- Data - At rest, in transit, and in use (databases, files, cloud)
- Users - People and AI agents with IDs, credentials, and permissions
Applications of the Cyber Defense Matrix
- CSF profile status and planning
- Responsibility assignments and handoffs
- Measurement and metrics
- Cybersecurity portfolio gap analysis
- Structural and situational awareness
- Vendor / product classification
CDM used for CSF profile status and planing
- The Cyber Defense Matrix (CDM) can represent Current vs Target Profiles
- Makes it easier to:
- Prioritise and allocate resources
- Monitor progress over time
- Communicate status to management & stakeholders
CDM for Responsibility Assignment & Handoffs
- The CDM is useful for defining who owns which responsibilities
- Clarifies the division of security tasks across departments
- Avoids unrealistic expectation that the security team handles everything
Benefit: Security is embedded across all business units, not siloed in the SOC.